"#OP_Germany" December DDoS Attacks: Some Observations
"Hacktivists" from at least 10 groups claim to try overwhelming numerous German and other NATO country targets.
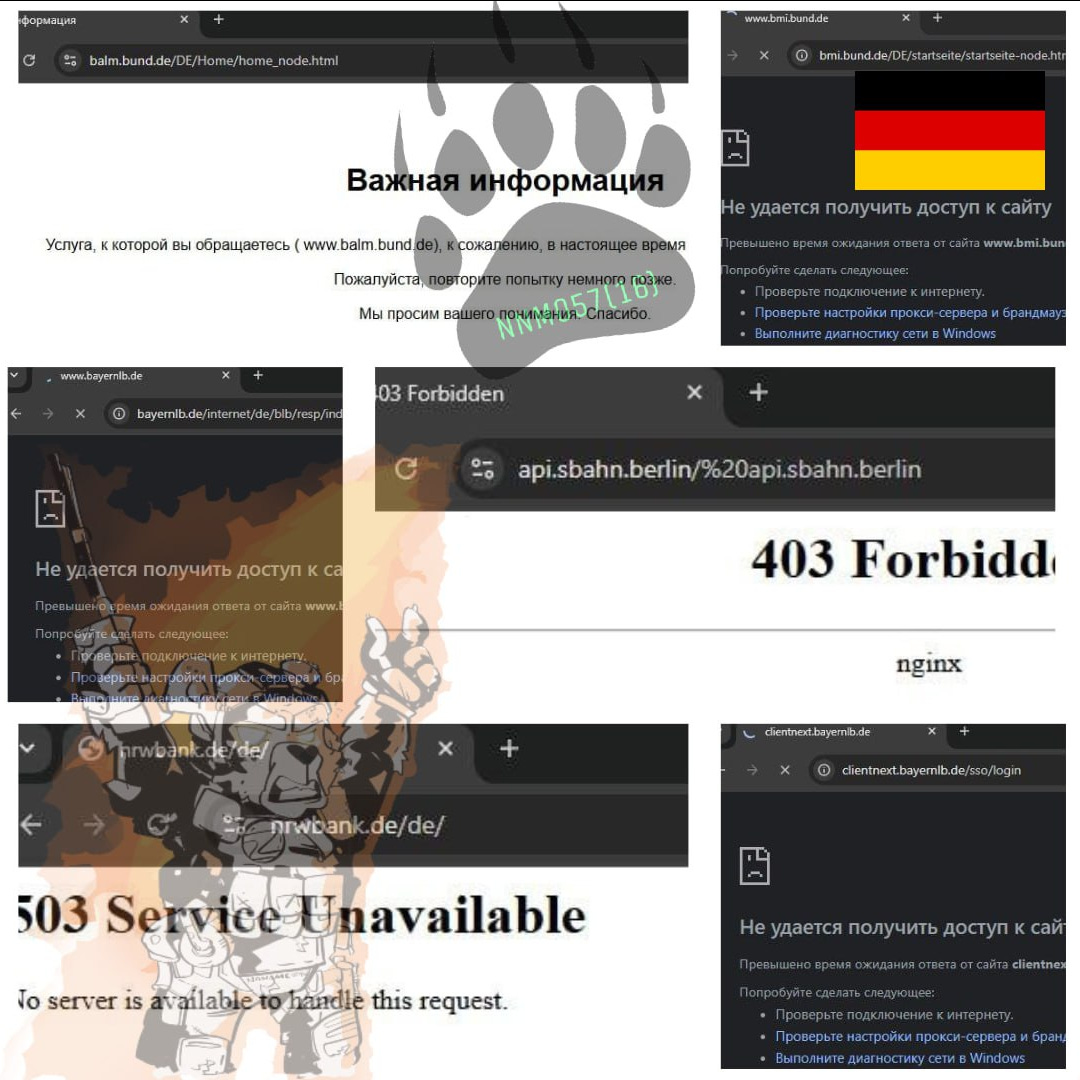
Last night’s pseudo-investigation had me returning to one of my usual customers, NoName057(16), when I saw that they were claiming anywhere from 9 to 17 successful website take-downs in 24 hours, largely of critical infrastructure (such as banking and transit).
Follow my main body of work on TheMoloch.com.
I do not feel comfortable giving Substack a portion of your money for reasons. Feel free to join the Substack newsletter for the reminders, but I don’t plan on having any exclusive content here.
Support Financially or Subscribe the Steady Newsletter
Donate to Mark on Buy Me A Coffee
Follow On Other Platforms
I’ll start with my typical DDoS’er preface: I’ve written several times about my positive feelings towards hacktivists. As a millennial who came into adulthood during the Arab Spring, it’s undeniable some of the good (even if you have to take issue with the methods or rhetoric) that groups who formed the template for many of today’s threat actors did during the late aughts/early twenty-teens. This is a large part of why some current threat actors still try to channel the memory of Anonymous.
I’ve also written several times about how absolutely full of it many of today’s “hacktivists” are.
The problem with DDoS is that, yes, at this point, it can be hard to take it terribly seriously… until you have to.
What happened? What Threat Actors?
Let’s get to it!
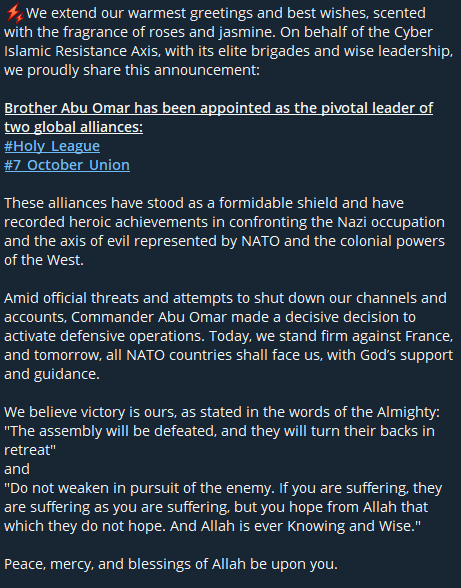
It looks like this wave of attacks was largely declared as yet another anti-NATO DDoS wave. The ones I followed were targeted at Germany. Some of the threat actors involved have also claimed the attack in support of Palestine. Here’s a post to this effect from Holy_League (a consolidation of numerous other “hacktivists”) before participating in the shenanigans:
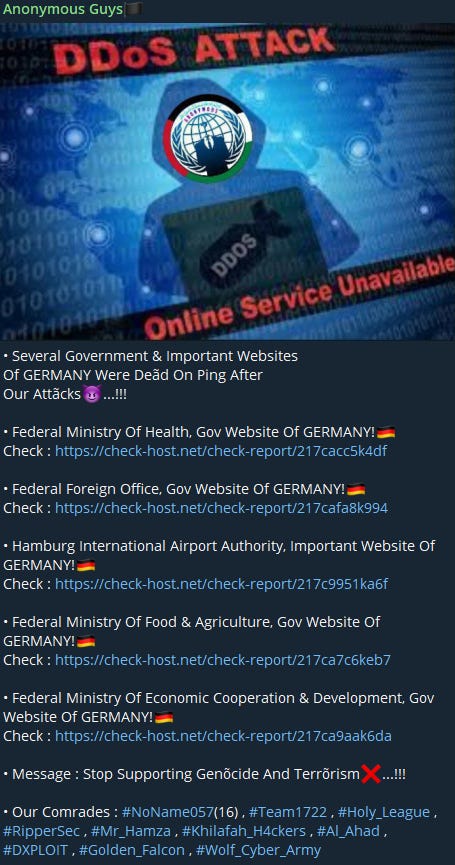
I’m not going to weigh in on how much stock I put into these, or what my feelings generally are, but the claims related to this campaign that I’ve seen the most from are Anonymous Guys and NoName057(16). Anonymous Guys tags the rest in this post:
While some of these groups (or their members, or their orbiters) have seemingly been involved in genuine support for Palestinians (no argument from me, there), I think it’s important to remember that many such groups are just covering for broadly pro-Russian sentiment. You can be as anti-colonial or anti-US-backed violence as you want, but this is largely what the rhetoric and motivation for these groups boils down to. I guess to these guys, what Russia is doing every day in Ukraine doesn’t fit their definition of “terrorism” or “colonialism”. It’s a bizarre, and—I suspect—disingenuous pattern that I’ll see daily when I hang out on Telegram.
Some hacktivist behavior is generally just signaling to the events-of-the-day for such shallow reasons as merch sales or general clout chasing. Some of them, such as Anonymous Sudan, at least attempted to sell services related to their work (access to their DDoS Botnet), but something that I find a little fascinating about NoName is that they’ve largely steered clear of that type of behavior, and have demonstrated some level of competence.
However, at the end of the day, DDoS just isn’t the threat it used to be.
What Was The Impact?
As is almost always the case with DDoS attacks on developed countries, every site claimed as a target in Germany has come back online.
You can take a look at some of the data I was able to gather (thanks to Shodan, Pulsedive, and CloudFlare) over the last 24 hours.
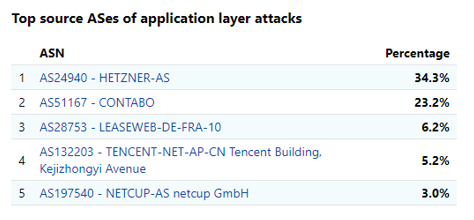
The majority of the more sophisticated, “Application Layer” DDoS attacks were largely coming from two server clusters, owned by Hetzner Online (AS24940) and Contabo GmbH (AS51167). Examination of both ASNs shows that they’re significantly over the average threshold of spam or DDoS traffic:
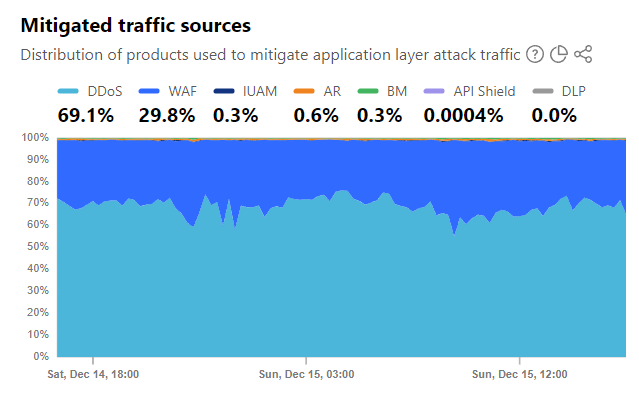
69 percent of DDoS traffic was denied in-transit:
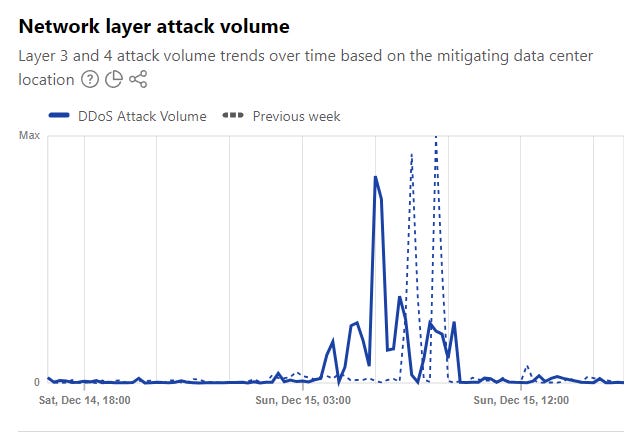
The attacks seemed to have peaked at around 0500 local time:
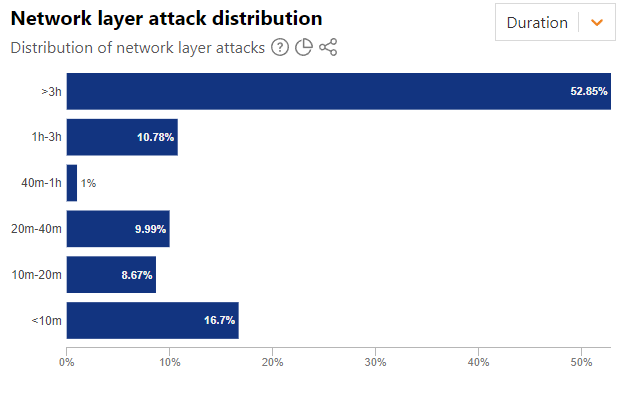
The attacks were sustained, with over half of DDoS activity in Germany lasting over three hours:
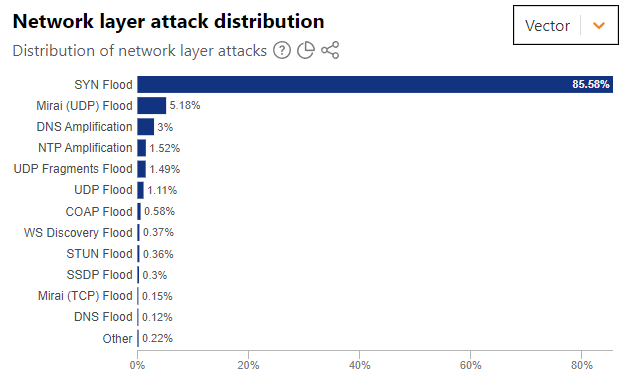
It looks like the Mirai botnet was implemented to some degree, though the much less resource-intensive SYN floods proved to be the tool of choice (though this makes sense with the sustained attacks):
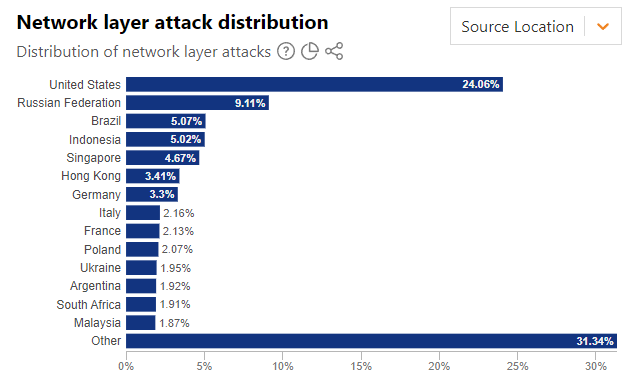
The two largest sources for the SYN floods were IP addresses based in the US and Russia, by quite a margin:
That’s really it. I don’t have some crazy conclusion or extremely valuable insight. I’m certain the DDoS attacks against Germany are going to continue. There are a few German and Canadian IP addresses I’m looking into that are likely related to the botnet, but I’m still figuring out where to land on with these mini investigations.
Until next time! Hail Moloch!