Threat Actor Drop: FunkSec RANSOMWARE
A new Ransomware threat actor has emerged, claiming over 30 victims in 10 days.
December is off to a dramatic start in the ransomware realm. Several new threat actors have taken the stage, including groups like LYNX, Sarcoma, and Brain Cipher.
I do not feel comfortable giving Substack a portion of your money for reasons.
Support Financially or Subscribe the Newsletter
Donate to Mark on Buy Me A Coffee
Follow On Other Platforms
However, one of the newest, and perhaps one of the most ambitious that’s come out is FunkSec. In the ten days since the group’s discovery, there have been claims of anywhere from 25-39 victims. T
They fall into the template of most current ransomware groups: encrypt and possibly steal data, deploying a double extortion strategy, and threatening to publicly release the stolen data if ransom demands are unmet.They operate off of a darkweb portal in the style of those such as LockBit, though this group has a flare for the retro/”hacker” vibe (how original).
They’ve also made claims that appear as though they’re acting as an Initial Access Broker on top of their ransomware activities.
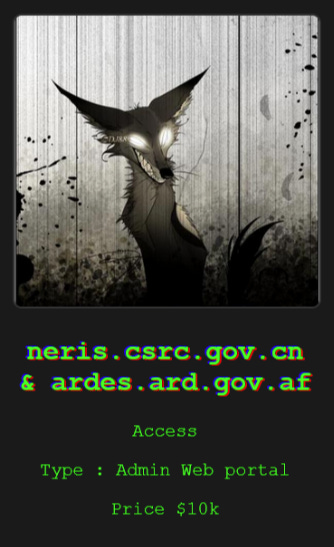
Alleged victims have included organizations from all over the world: the US, Afghanistan, India, France, Thailand, Peru, Jordan, the UAE, and nuermous others.
The group has claimed some strangely specific entities such as Afghanistan’s revenue department:
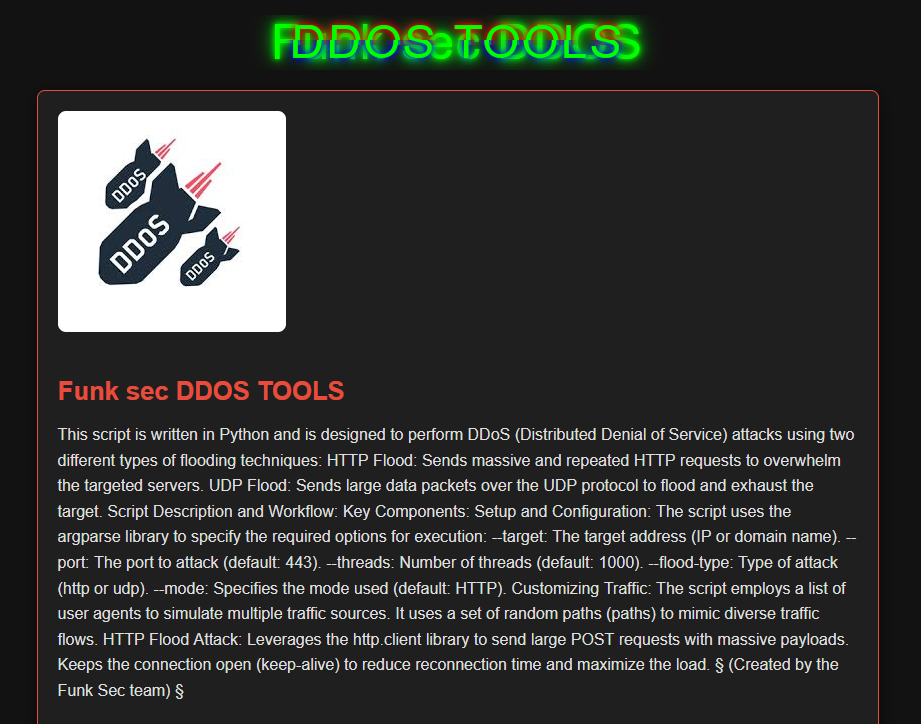
Another peculiarity of the group is that they offer access to a “free” DDoS tool.
Whoa whoa, hacktivism?
FunkSec has expressed intentions to target US entities, citing opposition to US support for Israel and aiming to weaken the Middle East due to its energy resources. This suggests that, beyond financial gain, the group may have politically motivated objectives.
Rules of engagement?
In a recent post, the group laid out a business model and a set of objectives in a statement from a member named "Scorpion". They announced their debut ransomware campaign (that began on the 3rd or 4th of this month), boasting of advanced double encryption technology capable of bypassing traditional security programs. They (proudly) outline the following tactics using a proprietary malware, “FunkLocker”:
Data Encryption (Extortion): Encrypts files with strong algorithms (namely, Fernet), rendering them inaccessible without a decryption key. Victims' essential data is held hostage to extract ransom payments.
Ransom Note Creation: Post-encryption, a ransom note is generated, providing payment instructions (via cryptocurrency) to regain access to encrypted files.
Psychological Manipulation: The ransomware alters the victim’s desktop background to reinforce constant fear and urgency. Notes often include threatening language or deadlines to pressure victims.
Efficient Deployment: Utilizing multithreading, the ransomware scans and encrypts multiple partitions simultaneously, to maximize their impact and speed.
File Renaming and Targeting: The malware renames some remaining files with on-the-nose names like "Ransomware" in order to mess with victims. Scorpion claims that their tool focuses on valuable file types (such as .pdf and .jpg files) to maximize leverage.
Stealth and Persistence: The tool operates undetected during the encryption phase, evading antivirus programs by mimicking common file extensions and delaying visible indicators until significant damage is done.
Broad System Impact: Eventually, the ransomware targets all partitions and directories, including external drives and desktop paths, to ensure comprehensive system compromise.
Deceptive Trust: They mention doing what they can to get users believing that paying the ransom guarantees decryption, exploiting desperation and fear.
I liked to them above, but for more specifics on FunkSec, check out Adam Price’s article about the group for Cyjax.